Key Takeaways:
- Digital immune systems enable enterprise resilience by combining AI-driven cybersecurity systems, automation, and real-time monitoring to prevent, detect, and recover from threats faster.
- A strong digital immune system architecture goes beyond tools, embedding security into development, operations, and governance for continuous protection and uptime.
- Successful implementation depends on strategy, people, and processes, not just technology, making digital resilience a core pillar of modern digital transformation security frameworks.
Over the last ten years, the frequency of data breaches and cyberattacks has surged, highlighting the urgent need for stronger cybersecurity measures.
A new report from CISA highlights that cyber attackers don’t just exploit vulnerabilities to break into systems; they also use them to run harmful code, stay hidden, and expand their control across networks. These attacks span multiple infrastructure layers, making it essential for organisations to adopt a proactive, automated security strategy.
One of the most effective ways to achieve this is by building a strong digital immune system that continuously detects, adapts, and responds to threats. But what exactly is a digital immune system, how does it strengthen cybersecurity, and how can businesses implement it?
Let’s break down its core concepts, challenges, and best practices.
What is a Digital Immune System?
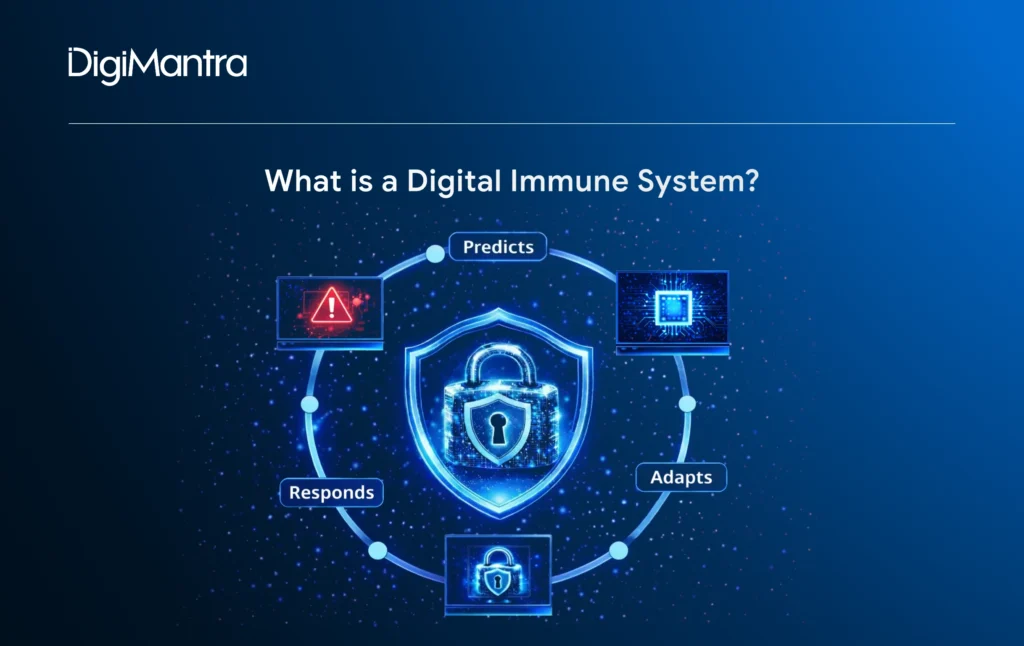
A digital immune system (DIS) is a unified approach that blends software engineering, testing, automation, and analytics to safeguard digital environments. Think of it as a cybersecurity model that goes beyond detecting threats – it predicts, adapts, and responds in real time. Unlike conventional, rule-based security frameworks, digital immunity is built to be intelligent, flexible, and continuously evolving.
Similar to how the human immune system functions, a DIS can independently spot irregular activity, contain potential risks, and restore normal operations with minimal human involvement. This level of protection is driven by a combination of core principles and advanced technologies working together for enterprise digital resilience.
Related Blog– AI-Enhanced Zero Trust Security- The Future of Cyber Protection
What are the Key Principles of a Digital Immune System?
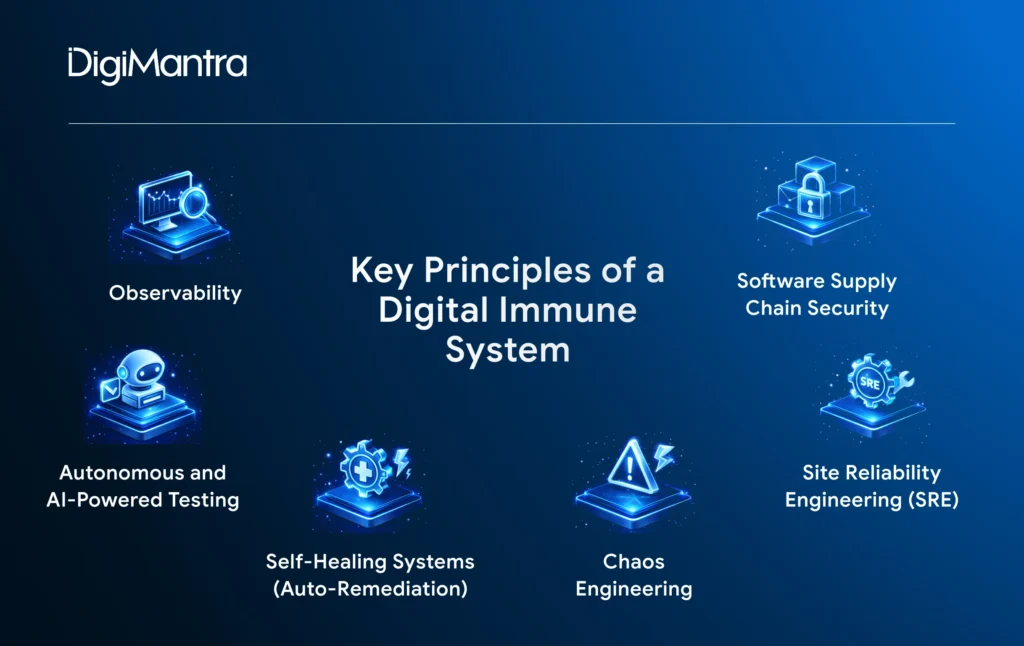
Here are six foundational practices and ideas to consider when designing a digital immune system (DIS) for your organisation:
Observability
Observability enables teams to understand system performance by examining generated data such as logs, metrics, and traces, i.e., the full path a request follows through an application. This visibility strengthens system stability by helping teams quickly detect irregularities and identify root causes of failures.
By monitoring user behaviour and application performance, observability also improves uptime and user experience. It can be implemented using tools like Prometheus, AppDynamics, or built-in cloud services such as AWS CloudTrail.
Autonomous and AI-Powered Testing
Automation is central to digital immunity, reducing reliance on manual intervention, and accelerating quality assurance. Autonomous testing systems powered by AI can manage the entire testing lifecycle, from test design and execution to analysis and optimisation, while learning from previous outcomes to improve accuracy and coverage.
In contrast, AI-assisted testing supports human testers by flagging anomalies and providing actionable insights, while final decisions remain with engineering teams.
Self-Healing Systems (Auto-Remediation)
Auto-remediation advances enterprise cybersecurity automation by allowing systems to not only detect problems but also resolve them independently. Through intelligent monitoring and automated fixes, organisations can reduce downtime, accelerate recovery, and maintain operational stability with minimal manual effort.
Chaos Engineering
Chaos engineering intentionally introduces failures into systems to uncover weaknesses before real-world disruptions occur.
Unlike traditional penetration testing, this approach simulates a wide range of scenarios such as service outages, performance bottlenecks, and network delays. These experiments can be conducted in staging or production environments, depending on system maturity.
Site Reliability Engineering (SRE)
SRE strengthens digital immunity by using automation and engineering principles to maintain system reliability at scale. It ensures applications remain stable during frequent deployments while improving user experience and fostering stronger collaboration between development and operations teams.
Software Supply Chain Security
The software supply chain includes all tools, processes, and third-party components involved in building and delivering applications. Securing it requires maintaining a clear inventory of dependencies through mechanisms like a software bill of materials (SBOM), enforcing version control, using trusted artifact repositories, and continuously monitoring third-party components throughout the development lifecycle.
Why Does Your Business Need a Digital Immune System?
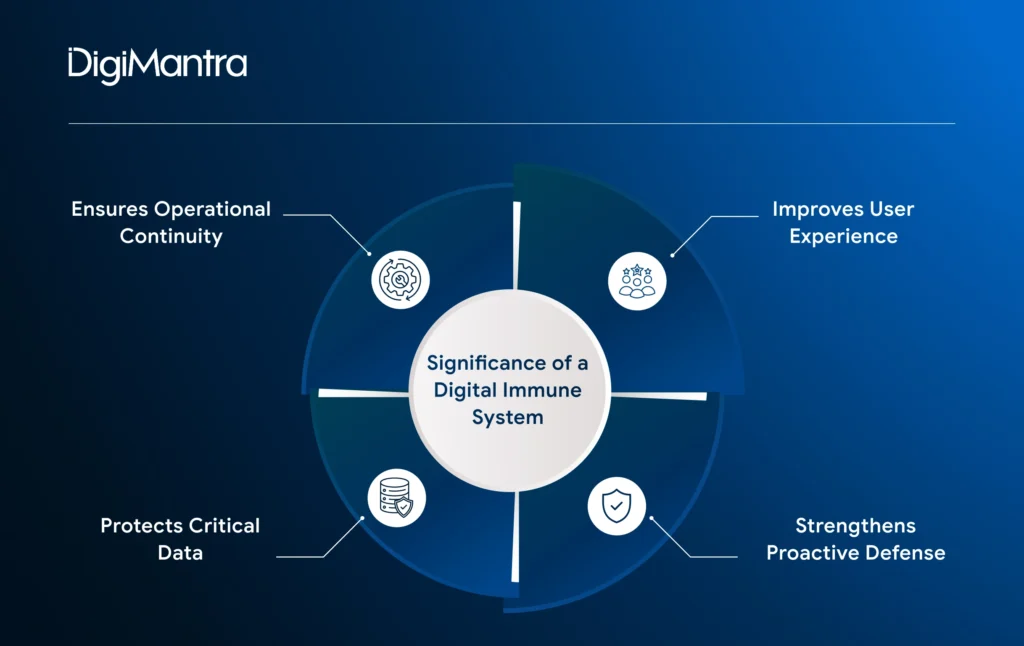
A digital immune system architecture strengthens multiple areas of an organisation, from customer experience and compliance to operational continuity and supply chain stability.
“Modern businesses must move fast, adapt to market shifts, and innovate continuously. But users expect more than basic functionality: they want speed, reliability, secure transactions, and seamless digital experiences,” says Joachim Herschmann, Senior Director Analyst at Gartner.
“Building a digital immune system begins with complete visibility across the entire digital ecosystem – from ideation and engineering through operations, security, and ongoing management. At its core, it’s about the customer. Research and real-world insights show that improving customer experience is the primary driver behind technology investments, which means delivering systems free from bugs, failures, and security risks is no longer optional, but it’s essential,” he added.
Here’s how it delivers measurable value:
- Ensures operational continuity: Digital immunity helps systems stay reliable and secure, even during cyber incidents or unexpected outages.
- Protects critical data: By identifying and closing security gaps early, it reduces the risk of breaches and data loss.
- Improves user experience: Automated recovery and reduced downtime enable seamless access to applications. Gartner estimates that organisations adopting DIS can achieve up to an 80% reduction in outages, significantly boosting customer satisfaction.
- Strengthens proactive defense: Continuous monitoring and automated remediation allow threats to be detected and neutralised before they escalate into major incidents.
How to Create a Digital Immune System for Your Business
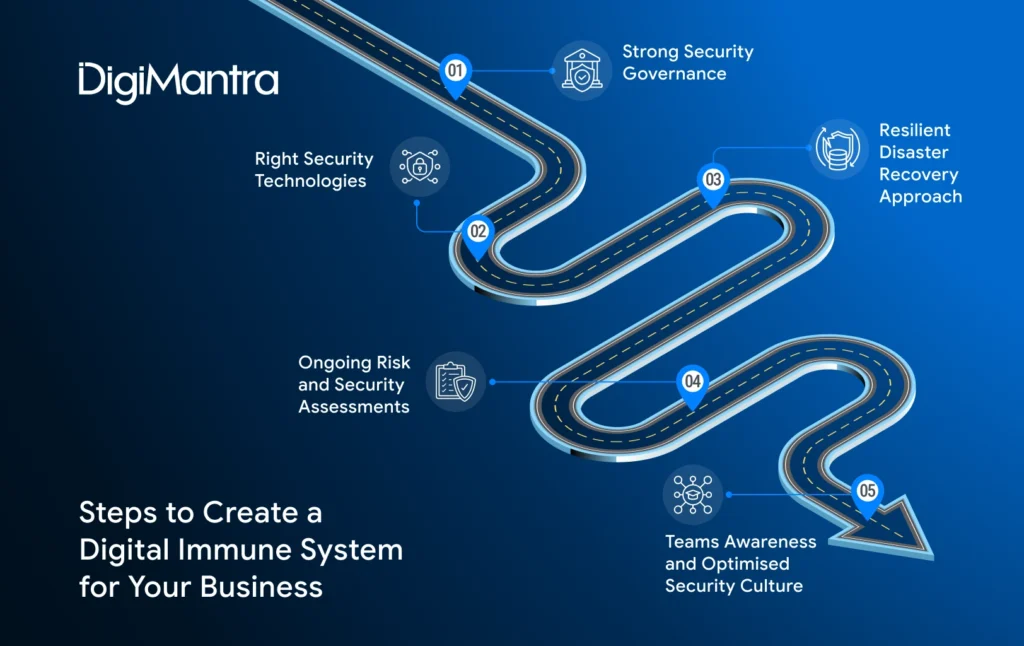
Once you decide to enhance your security posture with a digital immune system (DIS), the next step is defining the right digital resilience strategy. Your roadmap will depend on your business goals, current security maturity, and risk exposure. Typically, the journey starts with a detailed assessment of readiness and requirements, followed by a structured implementation plan.
Here’s how businesses can take the next steps:
Establish Strong Security Governance
Leverage proven digital transformation security frameworks and best practices based on your industry to design security policies aligned with your operational needs, compliance mandates, and risk tolerance. These policies should be reviewed and audited regularly to ensure they remain effective as threats evolve.
Deploy the Right Security Technologies
A digital immune system depends on an integrated toolset that protects multiple attack surfaces. This may include solutions for:
- Network protection: FortiGate (Fortinet)
- Endpoint security: Microsoft Defender, CrowdStrike, SentinelOne
- Security automation and response: FortiSOAR, KnowBe4 PhishER, Cortex XSOAR
These tools can be combined with custom-built solutions to strengthen your overall defense framework.
Build a Resilient Disaster Recovery Approach
A tested disaster recovery plan ensures business continuity during major outages or cyber incidents. Preparing in advance reduces downtime and supports compliance with standards such as ISO 27001, GDPR, and PCI DSS.
Perform Ongoing Risk and Security Assessments
Regular security testing helps uncover vulnerabilities before attackers can exploit them. Continuous assessments allow teams to evaluate risk impact, prioritise remediation, and stay ahead of emerging threats.
Educate Teams and Strengthen Security Culture
Employee awareness is a critical defense layer. Structured training programs help staff recognise cyber risks, follow best practices, and confidently use new security tools, transforming people into active participants in your security strategy.
Challenges in Adopting a Digital Immune System
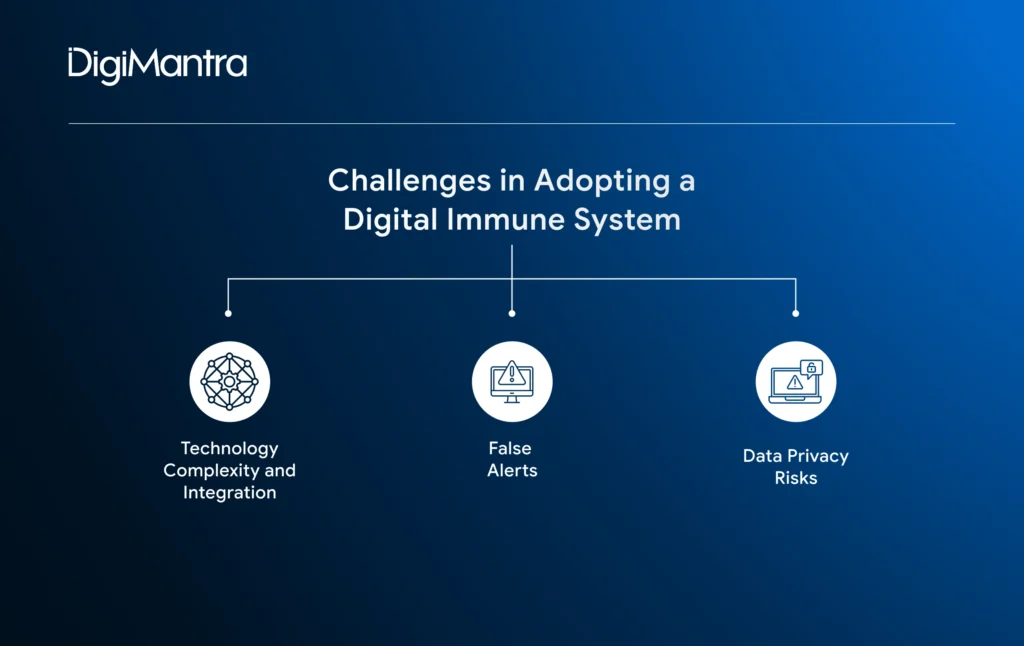
Although a digital immune system is essential for modern enterprises, its implementation can come with certain complexities and hurdles.
- Technology Complexity and Integration
A digital immune system brings together AI, automation, monitoring, and response tools, which can be difficult to integrate, especially in environments built on legacy infrastructure. This often requires significant time, expertise, and investment.
- False Alerts
AI-driven cybersecurity systems may initially flag normal activities as threats. Although accuracy improves as the system learns, early-stage deployments often need human oversight to fine-tune detection models and reduce unnecessary alerts.
- Data Privacy Risks
Because digital immune systems analyse large volumes of data, organisations must carefully manage privacy and regulatory compliance. Adhering to frameworks like GDPR is essential to ensure sensitive information is handled responsibly.
Final Thoughts
Digital immunity isn’t something you install, but it’s something you build. It comes from aligning automation, processes, and technologies to create a unified, end-to-end security framework. Achieving this level of protection goes beyond deploying tools; it requires embedding security practices into every stage of operations, from development and DevOps to infrastructure and governance.
While this journey may feel complex, working with an experienced digital transformation company makes it far more manageable. Their expertise helps you strengthen digital resilience with minimal disruption, ensuring every layer of your security ecosystem is implemented effectively and sustainably.

AI-FIRST ENGINEERING FOR MODERN BUSINESSES
Designed for performance. Powered by innovation.
 Product Development
Product Development Custom Software
Custom Software Mobile & Web
Mobile & Web
 AI & Automation
AI & Automation Cloud Management
Cloud Management Intelligent Systems
Intelligent Systems